
By Néstor Tejero on Oct 2017, in Web
WordPress is the most used content management system in the world and powers 60% of the sites that use a CMS on the Internet.. These are striking figures as, while they give us an idea of the platform’s colossal reach and potential, they also point out its vulnerability. This is because as the more popular the CMS, the more susceptible it is to malicious behaviour, as malware attacks.
There are a number of ways to protect your website. However, the most important steps you should take when thinking about your page’s security are related to the strength of your passwords and regular system updates to keep WordPress plug-ins and themes up to date. You should also be aware that third-party plug-ins and themes (both free and paid) are much more vulnerable as their codes are openly visible, making it easy for hackers to gather information. For this reason, we recommend that you further bulletproof your website by developing your own custom themes, as in this case the theme code is not publicly visible.
But what should I do if my WordPress is hacked?
Your system may have been infected by malware, a malicious code that infiltrates the system and acts against the requirements of the computer user. There are a variety of different types of malware created to serve a number of purposes. These include stealing personal information, rendering spam, or hacking computer systems.
Google flags infected domains with the warning “This site may harm your computer” and this has a disastrous effect on search engine rankings and website traffic as most users are deterred by the alert, leading them to use your competitors’ websites instead.
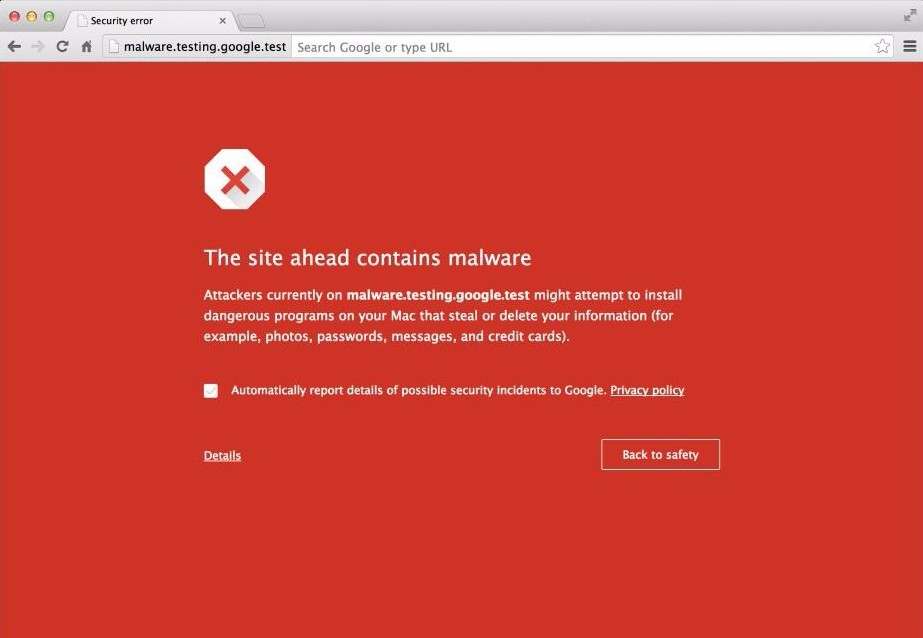
By following these simple steps you will be able solve this problem and avoid being penalised in the Search Engine Results Pages (SERPs):
- First take all plug-ins offline and activate a default WordPress theme, such as Twenty Sixteen.
- Next, back up all files and the webpage database on a local computer.
- Scan any files you have downloaded for malware using an Antivirus program. This will help you to determine where the virus is hiding, but the cleanup doesn’t end there. If you don’t already have an Antivirus program downloaded, we recommend the free version of Avast.
- Completely reinstall WordPress on your server using the latest fresh WordPress package from the official website.
- Reinstall all plug-ins from Wordress.org, as just as you did in step 4. Do not reuse the files you downloaded the first time around. Before downloading each plug-in, check that they are still supported by the community (If they are, they should be regularly updated with new versions). This is important, as it will help you to check if an outdated plug-in was responsible for your system getting hacked in the first place. If you discover that an original plug-in file is no longer supported, look around for a suitable alternative.
- If the antivirus program has not been able to locate any suspicious files in either the themes or uploads folders, re-upload them to their initial position using the FTP server.
- Reactivate themes.
- Change your WordPress and FTP access passwords.
- Remove any SPAM comments from your site. You can use the “Bulk comment remove” to clear large quantities of comments.
TIPS: “Invest in a hosting service that includes antivirus support. This dedicated add-on will help you to find any weak spots in your system and will make cleaning an infected WordPress site both quicker and easier.”
Request a review from Google
Now that you’ve completed the above steps, you system should be free of malware. Next you’ll need Google to confirm that your WordPress is no longer infected and remove the malware warning from your page.
To do this you’ll need to request a review from Google. To do this, go to Webmasters > Hacked Sites, and scroll down to “Security Issues Report”:
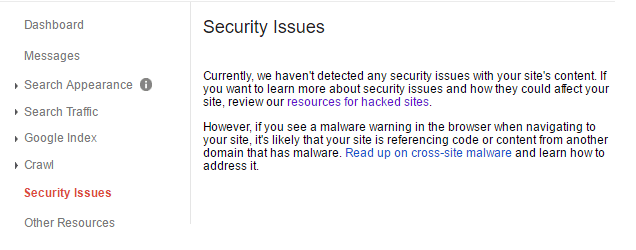
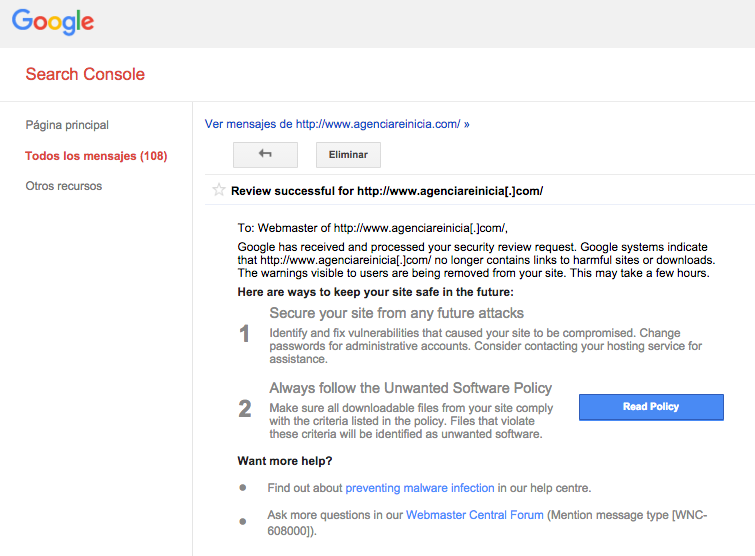
Log into your account and go to “Messages” or “Security Issues”. In both tabs you will find a message from Google letting you know that it has detected a virus on your system that could pose a risk to its users. To remove yourself from Google’s blacklist, select “Request a review” and write out the steps you have taken to clean your domain in the text box provided. You should receive a message from Google within 24 to 48 hours confirming whether the problem has been resolved or not.
For more information, check out the following tab in Google Webmasters.
You may find that after cleaning your WordPress, Google sends you the same alert malware again. In this case, the website code may not have been completely cleaned, meaning that the system is still vulnerable, or that later the virus may reactivate. Repeat the 9 steps listed above and troubleshoot to see what may have gone wrong the first time you cleaned your site.
Now go back to Google and request a second review. Once you have have sent the request and Google has confirmed that your website is no longer under attack, the malware warning should be removed from your site after 24 to 48 hours.
Has your WordPress been hacked? Do you need our help to recover your website? Contact us and we’ll help you.
Néstor Tejero
CEO and Consultant in Strategy and Marketing at Agencia Reinicia Co-founder Euromarketing Network



